Understanding Technology Security & Foreign Disclosure (TSFD) Pipes: A Comprehensive Guide
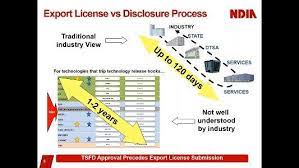
In today’s interconnected world, where technology plays a pivotal role in nearly every aspect of our lives, security is paramount. This is especially true when it comes to sensitive technologies that have the potential to impact national security and international relations. One crucial mechanism in managing this delicate balance is through Technology Security & Foreign Disclosure (TSFD) pipes. In this article, we delve into what TSFD pipes are, their importance, and how they function in safeguarding technology while facilitating international collaboration.
What are TSFD Pipes?
TSFD pipes are established procedures, protocols, and mechanisms implemented by governments and organizations to manage the release, sharing, and protection of sensitive technologies with foreign entities or individuals. These pipes serve as conduits through which controlled technologies flow, ensuring that the right information is shared with the right parties while mitigating the risks associated with unauthorized access or misuse.
Importance of TSFD Pipes
- National Security: TSFD pipes are essential for safeguarding national security interests by controlling the dissemination of sensitive technologies that could be exploited by adversaries or used against the nation’s interests.
- International Collaboration: In an increasingly globalized world, collaboration between nations and international organizations is crucial for technological advancement. TSFD pipes facilitate such collaboration by enabling the responsible sharing of technologies while protecting national interests.
- Export Control Compliance: The U.S. Government export control laws and regulations are in place to prevent the proliferation of sensitive technologies to unauthorized parties. TSFD pipes ensure compliance with these regulations by providing a structured framework for technology transfer.
- Protection of Intellectual Property: Sensitive technologies often represent significant investments in research and development. TSFD pipes help protect intellectual property by ensuring that sensitive information is shared only with authorized parties who agree to protect it.
How TSFD Pipes Work
- Classification of Technologies: Before sharing any technology through TSFD pipes, it is classified based on its sensitivity and potential impact on national security. This classification determines the level of scrutiny and controls applied to its transfer.
- Risk Assessment: A thorough risk assessment is conducted to evaluate the potential risks associated with sharing the technology with foreign entities. This assessment considers factors such as the nature of the technology, the capabilities of the recipient, and the intended use.
- Authorization and Control: Only authorized individuals or entities are allowed to receive the transfer of sensitive technologies through TSFD pipes. Strict controls are enforced throughout the process to ensure that the information is shared securely and in accordance with relevant export policies.
- Monitoring and Compliance: TSFD pipes include mechanisms for monitoring the transfer of sensitive technologies and ensuring compliance with established protocols. This may involve regular audits, documentation of transactions, and reporting requirements.
- Continuous Evaluation: The effectiveness of TSFD pipes is continuously evaluated and refined to adapt to evolving threats, technological advancements, and changes in geopolitical dynamics.
Conclusion
Technology Security & Foreign Disclosure (TSFD) pipes play a critical role in balancing the imperative of technological advancement with the need to safeguard national security interests. By establishing structured mechanisms for the responsible sharing of sensitive technologies, TSFD pipes enable international collaboration while mitigating the risks of unauthorized access or misuse. As technology continues to evolve and globalization deepens, the importance of robust TSFD pipes in ensuring the security of sensitive technologies cannot be overstated.
Comments